CYBER SECURITY


When developing a secure network, the following need to be considered:
Access--authorized users are provided the means to communicate to and from a particular network.
Confidentiality--information in the network remains private.
Authentication--ensure network user identity.
Integrity--ensure data is not modified in transit.
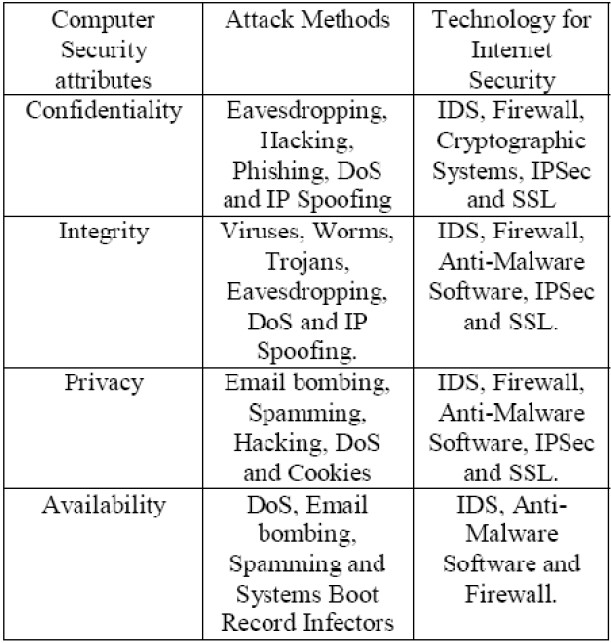
- Encryption
- Firewalls
- Intrusion Detection Systems
- Anti-virus⁄malware Software
- Secure Socket Layer (SSL)
